Basic Overview of SAML 2.0 SSO with IS 5.0.0
My aim is to explain a simple SAML 2.0 Single Sign-on (SSO) scenario with Identity Server 5.0.0 and Enterprise Store 2.0.0. The Enterprise Store consists of a Publisher web site and a Store web site. The scenario would be to enable SSO to Publisher and Store with Identity Server 5.0.0 where IS will provide SAML2 Web browser based acting as an Identity Provider or a Service Provider.
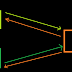
The diagram depicts the exact use case of the above mentioned scenario where we need to enable SSO to ES publisher and store via the WSO2 Identity Server. In the above use case both the ES Publisher and ES Store are the service providers and IS is the identity provider.
For the SSO to work, both the Publisher and Store are registered as trusted service providers in the Identity Server. Both the Publisher and Store implements the SAML 2.0 SSO and talks to the Identity Server via the assertion consumer URL defined in the publisher and store configuration files.
Step by Step approach of the visual Scenario
1. User tries to enter to the Publisher and Store via the corresponding URLs.
2. SAML 2.0 SSO will be configured for both the Publisher and Store as service providers in the Identity Server.
3.When the user hit the Publisher or Store URL, user will be directed to the IS login
4. User enters the login credentials ( Note - Here both IS and ES should be pointed to one common user database/AD/ldap etc)
5.If the user exists, the login will be successful.
The Actual Configurations for SSO and How to get it Working..
Prerequisites :
Identity Server 5.0.0 (Download : http://wso2.com/products/identity-server/)Enterprise Store (Download : http://wso2.com/products/enterprise-store/)
Configurations for both ES and IS to point to a common User database/store.
2.Open <ES_HOME>/repository/conf/datasources/master-datasources.xml file and add the datasource configuration for the database that you use for the shared user store and user management information. For example,
3. Open <ES_HOME>/repository/conf/user-mgt.xml file and point to jdbc/ustore.
<Property name="dataSource">jdbc/ustore</Property>
Note - ES will have the the jdbc user store as the default user store. So in the same file the jdbcUserStoreManager will be uncommented. Leave it as it is.
4.Open <IS_HOME>/repository/conf/datasources/master-datasources.xml file and add the USTORE datasource that you added to ES listed above. So now both IS and ES will point to the same database.
5. Open <IS_HOME>/repository/conf/user-mgt.xml and point to jdbc/ustore
<Property name="dataSource">jdbc/ustore</Property>
Note - IS will have the ldap user store as the default user store. So you have to comment out the ldap configuration and uncomment the jdbc user store in the same file. So both ES and IS will be accessing one common user store.
6. Open <IS_HOME>/repository/conf/embedded-ldap.xml and disable the embedded ldap by setting <Property name="enable">false</Property> within <EmbeddedLDAP> tags.
Now Both ES and IS will be pointing to one common user store..
Now Let's Register the Publisher and Store as Service Providers in IS
1. Start the IS pack
2. Go to IS Management Console > Main > Service Providers > Add
3. Give a unique name for service provider and click Register
4. Click on Inbound Authentication Configuration > SAML2 Web SSO Configuration > Configure
5. Fill on the details as follows for the publisher
Note - Assertion Consumer URL has my local/machine ip address. Configure it with your correct ip address and my ES is running on port 9444 which I have stated the offset as 1. This will be done in the future steps.
6. Fill on the details as follows for the store
Now the Service Providers are successfully registered.
Now Let's Do the Configurations for ES to Enable SSO
Publisher Configurations
1. Open <ES_HOME>/repository/conf/carbon.xml and change the offset to 1
2. Open <ES_HOME>/repository/deployment/server/jaggeryapps/publisher/publisher.json and change the values as follows :
"sso": {
"attributes": {
"issuer": "publisher",
"identityProviderURL": "https://10.100.7.57:9443/samlsso",
"keyStorePassword": "wso2carbon",
"identityAlias": "wso2carbon",
"responseSigningEnabled": "true",
"acs": "%https.host%/publisher/acs",
"keyStoreName": "/repository/resources/security/wso2carbon.jks"
}
}
Here the identityProviderURL will point to the IS and the issuer is given as publisher since when we were adding the service provider for the publisher we gave the issuer as publisher. Both should be the same.
3. Open <ES_HOME>/repository/deployment/server/jaggeryapps/store/store.json and change the values as follows :
"sso": {
"attributes": {
"issuer": "store",
"identityProviderURL": "https://10.100.7.57:9443/samlsso",
"keyStorePassword": "wso2carbon",
"identityAlias": "wso2carbon",
"responseSigningEnabled": "true",
"acs": "%https.host%/store/acs",
"keyStoreName": "/repository/resources/security/wso2carbon.jks"
}
}
Here also the identityProviderURL will point to the IS and the issuer is given as store since when we were adding the service provider for the store we gave the issuer as store. Both should be the same.
Now We are Done with the Configurations!!
Start the ES pack and Open up a Browser. Hit the Publisher URL > You should be directed to the IS login. Enter admin/admin username/password and sign in. Same with the Store.
Following is the IS login page that you will be directed to :
Following is the IS login page that you will be directed to :
Hope this post is helpful. Any feedback is welcome!







No comments:
Post a Comment